Creating A Website Using Kali Linux
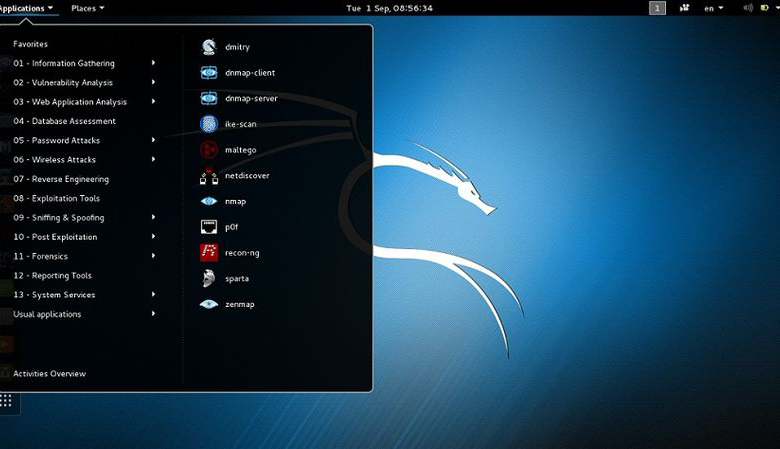
Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It is operated by Offensive Security Ltd. maintained and funded. Kali Linux was released on March 13, 2013 as a complete rebuild of BackTrack Linux and is fully compliant with Debian development standards. Kali Linux is a popular choice for penetration testers and security researchers as it comes loaded with a variety of tools and utilities to test the security of systems and applications. In this article, we will show you how to create a website with Kali Linux. We will use Apache web server which is the most popular web server in the world and the default web server in Kali Linux. We will also use MySQL database server, which is the most popular database server in the world and the default database server in Kali Linux.
As long as no other operating system or hardware is available, Kali Linux can be used as a normal operating system become. Git (as Git core), Mercurial, CVS, Subversion and Bazaar can be accessed in a stable environment. Unix/Linux made up 36.5% of web operating systems in 2018, ahead of Windows, which made up just under 33% of all operating systems worldwide. The Linux operating system is the most popular platform for web servers. The LAMP framework (Linux, Apache, MySQL, Perl and Python/PHP) consists of various databases and tools and is used for building internet software.
Reading: How to create a website using kali linux
Can I use Kali Linux for web development?
 Source: cstechnologyhub.blogspot.com
Source: cstechnologyhub.blogspot.com
As a result Kali Linux is an excellent choice for programmers, developers and security researchers alike, especially if you are a web developer. Kali Linux is also well suited for low power devices as it is compatible with devices like the Raspberry Pi.
Kali comes with a wealth of security testing tools as it was designed for penetration testing. In addition, it works well with low-power devices like the Raspberry Pi. It is based on Linux and Ubuntu and is a fast, lightweight operating system. Because Lubuntu’s apps are lightweight and use a minimal amount of desktop LxDI, they offer the best performance. Because it is a free operating system, hackers often use Kali Linux to conduct penetration testing and security analysis. Mac OS X’s popularity as an operating system for web designers and developers has increased dramatically. Manjaro’s user-friendly distribution makes development easy for a variety of applications.
Kali Linux is an excellent example of usage as it is a platform that provides advanced security tools. However, while working with Kali, it became painfully clear that there are no secure and open-source security tools. Clear documentation is also lacking.
However, if you are looking for a simple operating system that is beginner-friendly, Ubuntu may be the best choice for you. This is one of the most widely used and user-friendly distros. Ubuntu comes in different editions, which makes it suitable for a wide range of users. If you’re looking for a Linux distribution aimed at the average user, consider Debian. This application has an easy-to-use installer and is ideal for those looking for stability. Several versions of Debian are available alongside the Ubuntu distribution, making it suitable for a wide range of users. If you’re looking for a Linux distro with a more professional feel, Ubuntu is a good place to start. Kali Linux is a fantastic choice for digital forensic investigations, but it’s not the best choice for beginners. In terms of learning, Ubuntu is an excellent choice for those looking for a beginner-friendly operating system.
Kali Linux: Great for pentesting, but not for everyday use
It does well for pentesting and reconnaissance, since it has a large number of pre-installed software programs. Due to its scarcity of resources, it is not suitable for everyday use. The Ice Python language is used in Kali Linux, which is similar to other Linux distribution languages.
Is Kali Linux a website?
See also: Archive items manually
 Image credit: techdhee.in
Image credit: techdhee.in
No, Kali Linux is not a website. It is a Debian-based Linux distribution designed for digital forensics and penetration testing.
Linux is an excellent distribution for developers because of its security features. This operating system is compatible with Live DVDs, as is Tails. This feature leaves no trace after a user uses it, so there is no evidence of an information breach. The Kali Linux operating system is part of the public domain under the GPL.With Kali Linux, you can protect yourself not only from the cybercrime threat but also from the identity theft threat. Kali Linux runs a free, simple and highly secure operating system. To allow hackers to modify Kali Linux, all of its code can be found on GitHub. The kernel includes a fully customizable environment that makes it easy for hackers to use.
The Kali Linux operating system is free and open source, making it the ideal platform for penetration testing and security auditing. There are several hundred tools available to help you with a variety of information security tasks such as: B. penetration testing, security research, computer forensics and reverse engineering. Due to its robust yet user-friendly design, Kali Linux is a good platform for anyone interested in a career in information security. This is a free, open-source program, making it an excellent choice for anyone interested in a career in information security.
Identifying Web Technologies with Linux We
Linux Web, a project that identifies various web technologies, serves as a repository for plugins that can be used by organizations and projects.
What is Httrack in Kali Linux?
HTTrack is a free one and easy to use offline browser utility. It allows you to download a World Wide Web site from the Internet to a local directory, build all directories recursively, and transfer HTML, images, and other files from the server to your computer. HTTrack arranges the relative link structure of the original page. Just open a page of the mirrored website in your browser and you can browse the website from link to link as if you were viewing it online. HTTrack can also update an existing mirrored website and resume interrupted downloads. HTTrack is fully configurable and has an integrated help system.
Using a service like httrack, you can connect to a local directory and download a website from the Internet. The relative hyperlink structure or meta-link structure of the first site is also linked to it. After pressing Enter, the command will exit and a list of filters and options will appear. With its sophisticated features, H.T.Track Website Copier is one of the most advanced tools available. There is a possibility of creating a duplicate website if the software is used for educational purposes. Wget, a free, open-source alternative, may be preferable to Httrack. How to Copy a Website on a Mac? After releasing the command key while holding ll, you can see the address field by pressing L followed by C.
Risks of using Httrack on an untrusted computer
How can I use this software on my own computer? Although there are no particular risks associated with using HTTP on an untrusted computer, it is always recommended to exercise caution when installing software from unknown sources. Additionally, if you choose to review the code, you can make changes that could potentially introduce new vulnerabilities; Also, HTTrack is open source, so anyone can access it. Finally, remember that the tool is not designed to download or remove spyware programs; rather, it serves to monitor and remove programs that pose security threats.
Kali Linux documentation page
Kali Linux is a Debian-based distribution that aims to provide a broad range of security tools. The Kali documentation page provides information on installing and using the various tools available. It also includes a section on how you can contribute to the project.
Kali Linux: The perfect tool for information security
See also: How to Start a News Website in 12 Easy Steps
This open-source Debian-based Linux distribution is for Security thought -related tasks such as penetration testing, security research, computer forensics and reverse engineering. Kali Linux is a popular platform for hackers because of its security analysis, auditing, and penetration testing features that make it an excellent tool for protecting information.
Web Operating Systems
An acronym for “appear”. A web operating system (also webOS or web OS) is a type of rich internet application that includes some applications (such as file storage and permissions) and some features that are configurable through the operating system. There is usually a web browser you can use to access it, e.g. B. from the Internet.
WebOS is a web-based application that mimics the application functions of an operating system (usually using AJAX or Flash). Therefore, it typically runs in a web browser so that it can be accessed at any time. Webtop is also available, although there is no operating system support, similar to Web 2.0 applications. WebOS and Ajax start pages like yourminis, Netvibes and Pageflakes overlap in intent and function. An operating system, such as a web operating system, typically includes a full development environment, as well as email clients and other desktop software replacements. (See the Lite section for more information.) Open source CMS.com offers a number of options for testing these systems.
Website Penetration Testing
Petration testing, also known as penetration testing, is a type of computer security vulnerability assessment that involves a real world cyber attack on your Computer system to ensure vulnerabilities are exploited. Penetration testing, which is widely used to increase web application security, is often performed on a web application firewall (WAF).
Almost one in ten companies is at risk of being exposed to an undetected vulnerability. Penetration testing is a method used by hackers to assess the severity of existing vulnerabilities. It involves launching a hacking attack on an application. You can perform both automated and manual vulnerability assessments. Penetration testing, on the other hand, is a manual process, typically performed by a security engineer with specialized knowledge of the industry. Both vulnerability assessment and vulnerabilities vulnerability vulnerability vulnerability vulnerability vulnerability vulnerability vulnerability vulnerability vulnerability vulnerability vulnerability vulnerability You can anticipate potential accidents by using VAPT. This usually improves the risk management of your website.
The three phases of web service testing are information gathering, testing, and vulnerability assessment. An OSINT is information that is publicly available about your target, such as: B. name, email address, etc. Around 270 different server types are included in the Nikto tool, which is intended to detect vulnerabilities. The Burp Suite includes a built-in proxy that intercepts traffic between your browser and the target website you’re testing. Rapid 7 has a Ruby based web application called Metasploit. The data fields on the page can be fuzzed with sqlmap to see if any SQL injection points have been inserted. Xsser is a relatively new and lightweight tool for identifying and exploiting XSS flaws during website penetration testing.
The Health Insurance Portability and Accountability Act (HIPAA) sets out a number of regulations for the protection and disclosure of health information of patients. Companies must develop policies and procedures for handling customer data as part of the SOC II standards. Many companies, including banks and healthcare providers, are required to comply with the ISO 27001 standard. The main requirements for ISO 27001 compliance are the development and implementation of an Information Security Management System (ISMS). The identification and assessment of information security risks and the implementation of controls to reduce these risks. It is important to regularly monitor and evaluate the effectiveness of the ISMS. It is important that your company conducts regular website penetration testing to ensure its audits are successful.
Depending on how many scans are performed, website penetration testing costs can range from US$349 to US$1499 -dollars per scan. The Astra community of experienced security professionals will test your website to ensure it’s secure. They will also tell you the steps to fix the problem and can even help you or your developer with patching.
Penetration Testing: Techniques and Benefits
That’s it It’s possible for testers to gain access to a target system in an external penetration test using a variety of techniques including, but not limited to, hacking into networks and gaining access to systems. Attempting to gain access to a person’s system settings by cementing them against them. The compromise of security measures and unauthorized access to sensitive data. Internal penetration tests are not uncommon. This type of testing can be used to determine the vulnerability of web applications to attacks from within. Web application vulnerabilities can be exploited by hackers in a variety of ways, including but not limited to compromising security measures to gain access to sensitive data. An attacker can exploit cross-site scripting flaws to inject malicious code into web pages. Attempt to tamper with the system by changing the system settings. Penetration testing has a number of benefits. These tests can potentially identify vulnerabilities that an unauthorized person can exploit. In addition, they can improve the security of the system by identifying areas where improvements are needed.
See also: How to Start Dropshipping With WordPress
.